The Rise of DNS over HTTPS
Online security and privacy got a pretty big boost with the rise of HTTPS, this can be attributed to companies like Let’s Encrypt, but also security researchers like Scott Helme. This means that most of your traffic and online communication is now encrypted and can’t be read by other people. You might wonder if this is such a big issue, and the answer is simply yes, it is. This is due to the fact how the internet is built, all your traffic will pass a few other computers (or servers) before it reaches its destination. The most important inbetween hop is probably your internet service provider (ISP).
Well, security is solved, we can all go home! Unfortunately, we just move on to the next frontier, the domain name system (DNS). This system is a protocol that translates common domain names such as example.com to a number that can be understood by a computer, the IP address. You can compare this with a giant version of the yellow pages for internet addresses, linking human readable names with machine readable addresses. Unfortunately, this protocol works in an insecure way, all these requests are sent in plain text over the internet. And as we now know, this traffic passes a few other computers before reaching it’s destination, so several people might read these requests you make. Therefore, we are in need of a protection mechanism, enter DNS over HTTPS (DoH).
Who is interested in this DNS request data?
The main threat is your ISP, they keep records on all your DNS requests, sometimes for more than a year. There are cases were they have been selling this data to third parties. Moreover, they can also interfere with the responses to DNS requests, in this way they could point you to another website than you’re actually requesting. This happens for example when you request a non-existing domains, they sometimes redirect you to a page full of ads, so they can make money of this. Furthermore, DNS requests have been used to block certain websites, usually after a court order. In some countries this leads directly to censorship by oppressive regimes, but even in more democratic countries this can be used to limit free speech. For example in the US, where net neutrality is not a thing anymore, ISPs can give preference to certain traffic over other traffic, e.g. allowing Facebook traffic over Netflix traffic. This leads to a pick and choose, where ISPs could for example slow down or eliminate traffic of big competitors.
Another very common practice is the monitoring of DNS requests in an enterprise setting. Companies tend to look at the internet traffic of their employees, giving security as the reason to do this. However, I strongly believe we cannot solve security at a network level, therefore, we need to move to fully encrypted traffic such that we don’t have to worry about anything on the network. As a side effect this means that we cannot try to protect an enterprise network using old techniques like filtering traffic or looking at specific DNS requests, instead we solve these issues at the end point itself, i.e. laptop, phone, or other device employees use. This approach is much more in line with modern ways of working, where people work from all sorts of places, not only the company network, and people use all sorts of devices, maybe not even company owned. And articles such as these make me angry, where for the benefit of some network security products they demonize some good measures such as DoH. It is the lobbying of certain security product vendors that keeps us back in reaching some decent affordable security at enterprises. Don’t forget if you are in charge of security at an enterprise, you are not an oppressive regime, you just try to protect your data and users.
How do we protect against these threats?
As mentioned before, HTTPS, the secure version of the standard HTTP protocol, helps a lot against most remote threats on your network traffic, but now we can also protect our DNS requests by using DNS over HTTPS. This means that instead of its own unencrypted protocol, we can make all DNS requests look like normal HTTPS traffic. Any malicious actor on the network cannot distinguish this traffic from normal HTTPS traffic. Moreover, they are not able to read your DNS requests, nor can they tamper with the answers.
This isn’t the first attempt at a more secure DNS system. Probably the first attempt was DNSSEC, a system that could prove the authenticity of a DNS response, i.e. to make sure the IP addresss that you got as an answer is indeed the website you were looking for by using cryptographic signatures. This can still exist next to DoH, of course. However, a major downside of DNSSEC is that everyone should support it to get the full security benefits. Next, they introduced something called DNS over TLS which given the name seems very similar to DNS over HTTPS. However, the big difference is that DNS over TLS created its own protocol adding a layer of TLS around the original protocol. To the contrary, DNS over HTTPS doesn’t invent anything new, it just translates the DNS queries and sends them through a normal HTTPS connection, these are existing components combined in a more secure way. That is also the reason that I believe DNS over HTTPS is the right choice to protect our DNS traffic. Moreover, you don’t need everyone else to adopt it to receive its security benefits.
The only thing needed is your computer doing right queries, which I’ll briefly discuss in the next section. In general, I believe the operating system should be the one doing these queries, but at this point mainly browsers are doing experiments with the DoH protocol. This is a good effort and will make DoH more mainstream, but I think we will see a shift to the OS at some point. On the other end, we need a DNS server that can actually receive such requests. At this point the main actors are Google and Cloudflare, but there are also smaller players such as Quad9. Cloudflare started this service last year and did a big marketing campaign to promote DoH, this sets things finally in motion to more secure DNS requests. It is clear that you need to put trust in either one of these companies, to enhance general privacy and security it would be great if we would see more providers following.
If you are interested in further technical details, the best intro to read is probably this one by Mozilla or you can read this blog post by Alec Muffett.
In practice
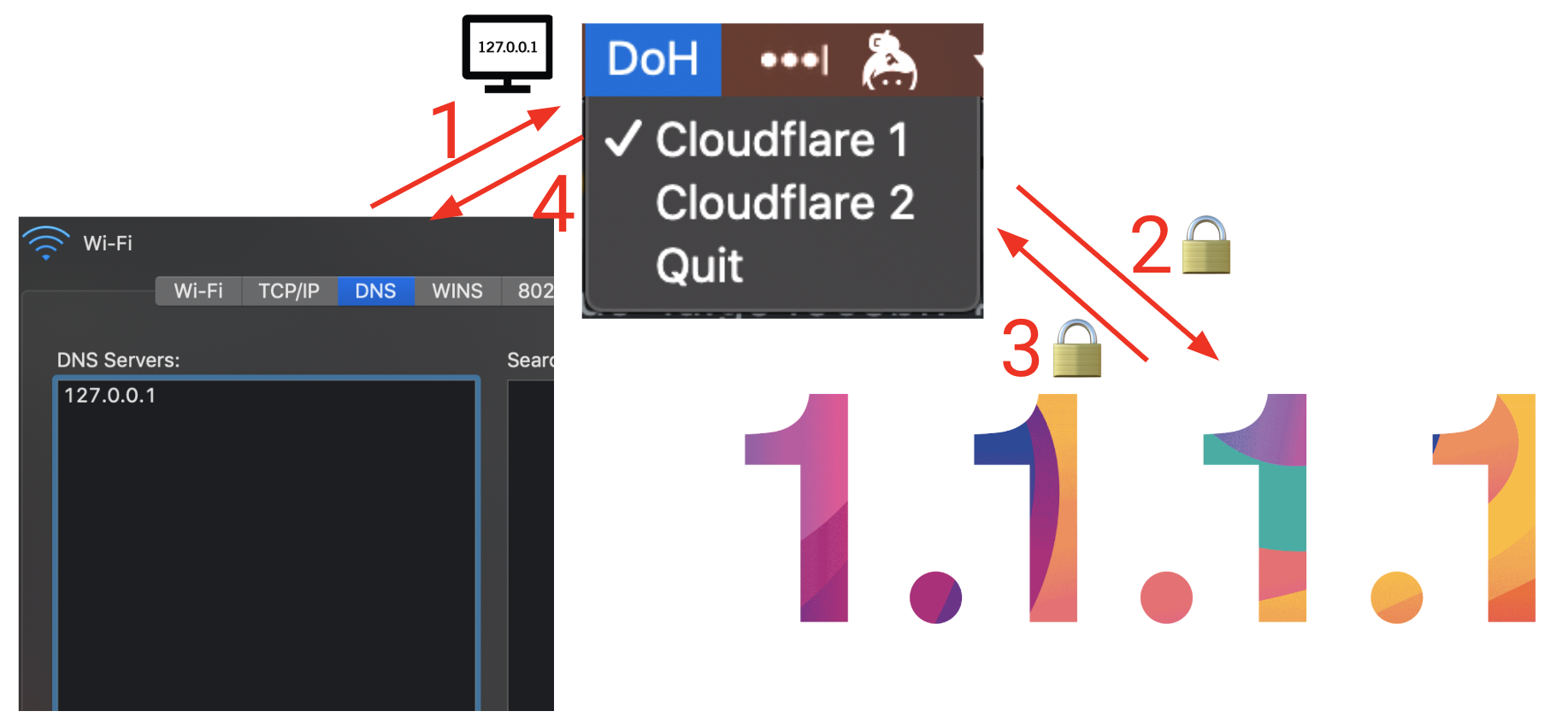
I wrote a little DNS client that you can run on your computer that will redirect all DNS requests to Cloudflare’s DoH resolver, or you can add other endpoints as well. When running this client, you have to set your DNS settings to point to localhost. This is a very experimental tool and might require some technical knowledge to easily run.
Other solutions are provided by using Firefox, they have a setting where you can use DoH, which resolves to Cloudflare. In the future we will also see this appearing in Google Chrome, they obviously will resolve to their own DoH resolver. Cloudflare itself also has a mobile app that introduces DoH on your mobile phone. In general I believe this should be something that can be solved by your OS instead of your browser, as your browser is not the only one making DNS requests, other software can do so too. But apart from Android 9, I haven’t seen any introduction of DoH in an OS.
DoH is coming, if ISPs, governments, or enterprises like it or not. But in general for users, this is a good thing, it will enhance your online security and privacy. I’m looking forward to this progress.